How to Protect Employee Confidential Information: Rules and Solutions

Your company gathers a lot of sensitive employee information, including social security numbers, medical records, dates of birth, and daily activity on work computers. Protecting this data is not only a matter of ethics and trust; a data breach will mean significant legal and financial repercussions.
So, how do you secure employee confidential information? You should start by identifying the full scope of sensitive data, from the obvious, such as personal identification details, to the often-overlooked, such as employee monitoring analytics. Then, you build your security system. This means enforcing strict access limits, encrypting data, and transforming your workforce from a potential vulnerability into your first line of defense through consistent training.
The path to robust data protection is systematic. Let's discover the essential categories of information you're responsible for, the legal framework that requires protection of this data, and the practical, actionable solutions that will help you secure it.
What Needs Protection and Why
Before building any defense, you must first map the territory. What exactly is employee confidential information? Usually, we think of it as personal identifiable data, for example, a Social Security number or bank account details. However, sensitive information goes far beyond these limits in practice.
What is Employee Confidential Information?
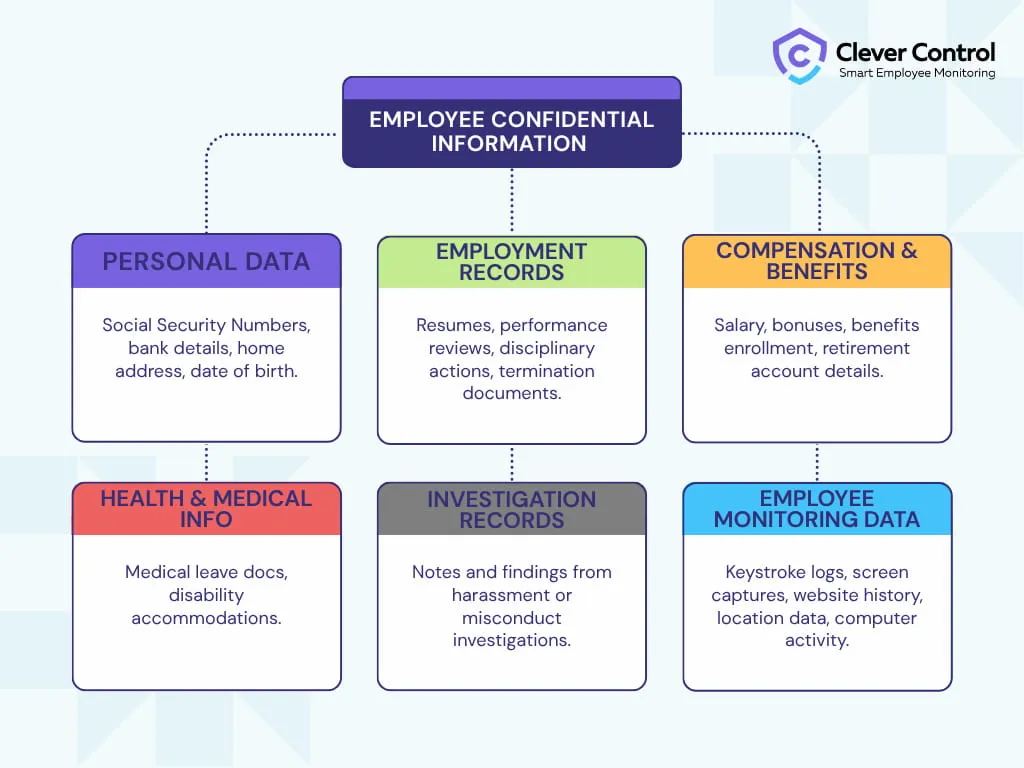
Think beyond the personnel file. You create sensitive data throughout the entire person's employment, from the recruiting call to the final exit interview. This data can be categorized into:
Personal identifiable information (PII)
This is some of the most sensitive data that can identify an individual. If compromised, it can lead to identity theft and other serious consequences. It's the non-negotiable must-protect list:
- Social Security numbers
- Home address and personal contact information
- Date of birth
- Bank account details for payroll
- Marital status and dependant information
Employment records
At first glance, these records may not seem as significant, but their confidentiality is key to maintaining fairness and trust. Employment records are:
- Job applications and resumes
- Interview notes
- Employment contracts
- Performance reviews, disciplinary write-ups, and formal warnings.
- Termination records and resignation letters.
Financial data
Perhaps the most sensitive topic for most employees, this information must be guarded with extreme care to prevent internal conflict and external targeting.
- Salary
- Wage details
- Bonuses
- Incentive pay
- Benefits enrollment forms (health, dental, life insurance)
- Retirement plan account details and contributions
Health & medical information
This category is governed by a web of strict regulations that may vary in different countries and includes:
- Leave certifications and medical documentation
- Records of reasonable accommodations
- Workers' compensation claim files
- Drug test results and physical exam reports
- Doctor's notes submitted for absences
A critical best practice, often legally required, is to store these records in a separate, secure medical file, entirely apart from the general personnel file.
Investigation records
Investigations of harassment, discrimination, or other misconduct create highly sensitive data. If compromised, this data can ruin not only the investigation but also workplace culture and lead to legal consequences. Investigation records are:
- Written statements of complaints
- Witness interview notes and summaries
- Evidence collected (emails, reports)
- Final investigation reports and conclusions
Employee Monitoring Data
The data collected by monitoring software is a detailed digital profile of your employee. Treat this data with the same seriousness as you would a personnel file.
- Keystroke logs and website usage history
- Screen captures and activity levels
- GPS location data from company vehicles or devices
- Email and communication metadata
The Legal Framework
Many of the above types of employee confidential information are protected under specific statutes or regulations. However, the scope of protection varies from jurisdiction to jurisdiction and from country to country. In the United States, for example, employers must comply with the Americans with Disabilities Act (ADA), which requires that employee medical information be kept confidential and stored separately from general personnel files.
Other notable regulations are:
- The Family and Medical Leave Act (FMLA). Under it, medical certifications and details related to an employee's leave must be kept private.
- The Genetic Information Nondiscrimination Act (GINA). It protects employees' genetic information and family medical history.
- The Fair Credit Reporting Act (FCRA). When employers conduct background checks for employment decisions, this regulation imposes strict obligations on them.
Additionally, some states have enacted comprehensive privacy laws. One example is California's Consumer Privacy Act (CCPA/CPRA), which grants further rights and protections to employee data in those regions.
In Europe, the General Data Protection Regulation (GDPR) is the main privacy regulation. Any organization in the EU that processes personal data (including employee confidential data) must follow several key principles: a lawful basis for processing, data minimization, data protection, and respect for individuals' rights.
If your workforce spans multiple jurisdictions, you must consider privacy regulations in each of these jurisdictions. A one-size-fits-all approach is a recipe for compliance failure. Consulting a legal expert who specializes in the employment and data privacy laws of each country where you operate is a wise choice that will help avoid potential legal trouble.
A 5-Pillar Strategy for Protection
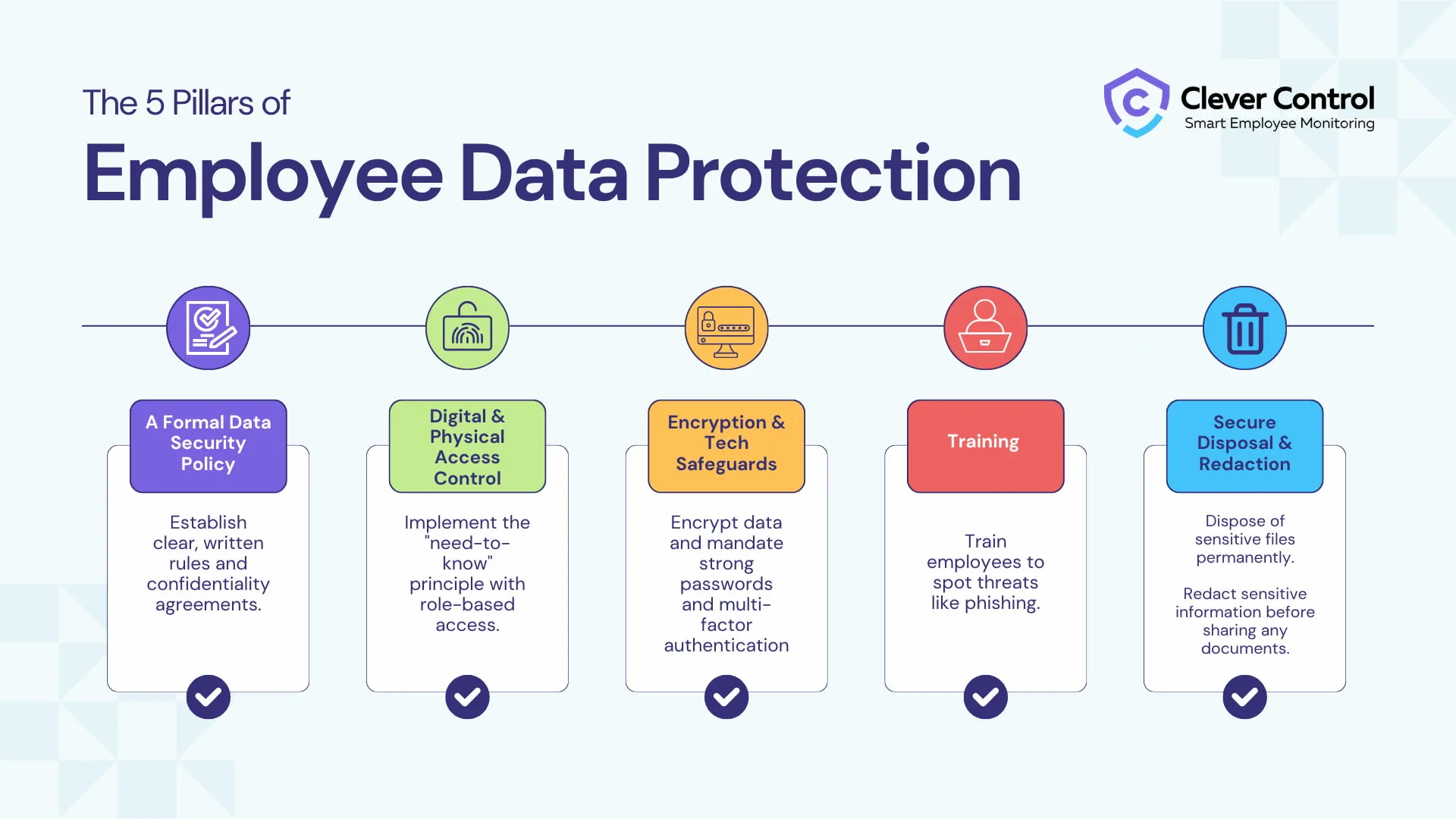
So, how do you protect employee confidential data? We suggest five pillars upon which you can build a solid data protection system.
Pillar 1: A Comprehensive Data Security Policy
Data protection begins with commitment. A comprehensive data security policy serves as your organization's constitution for information handling.
What to do:
- Craft a clear, comprehensive document. It must precisely define confidential information, chart clear handling procedures, and outline the real-world consequences for breaches.
- Secure signed agreements. This will make the data handling policy personal. Signing the policy will transform a general rule into each employee’s personal commitment, for which they will be accountable.
Pillar 2: Access Control and Limitation
A database without access controls is like a house with every door open. In a solid data protection system, no one should have access to data unless their job demands it.
What to do:
- Implement role-based access controls. Create subaccounts in your HR systems, employee monitoring software, and other data storage systems, so that managers and HR personnel can see only the information they absolutely need. The marketing team has no business in the payroll folder, just as accounting doesn't need the product development roadmap.
- Don't neglect the physical world. For every locked digital file, there should be a corresponding locked filing cabinet. Control keys meticulously. The most sophisticated encryption is useless if someone can simply walk off with a paper folder.
- Keep access logs for data storage systems. Knowing who accessed what and when creates an invaluable audit trail.
Pillar 3: Data Protection with Tech and Physical Tools
You should always protect employee confidential information, regardless of how it is stored and used, whether it’s on a server, sent by email, or lies in a folder on the manager’s desk.
What to do:
- Encrypt all sensitive data. Treat encryption as a default state for all employee confidential information, both at rest on your devices and in transit across your network.
- Use multi-factor authentication. Passwords are no longer a total protection on their own. Multi-factor authentication requires a second proof of identity and adds an extra layer of security. It is a free and effective way to lower the potential risks.
- Enforce a clean desk policy. As surprising as it may seem, a cluttered workspace or an unlocked computer presents an excellent opportunity for a data breach. A simple rule - securing all documents and logging off before walking away - builds your first line of defense and can significantly lower security threats.
- Draw a hard line on personal devices. The convenience of using a personal phone or laptop for work is a Trojan horse. Prohibit it. You cannot control what potentially insecure apps the employee installs on the device or who they lend it to.
Pillar 4: Training
Technology can do many things, but it cannot replace human judgment. Your team is either your strongest shield or your weakest link. Training is what makes the difference.
What to do:
- Make training a narrative, not a lecture. Ditch the bullet-point slides. Use real stories to teach employees how to spot a clever phishing email or resist a manipulative social engineering call. Connect the dots between their actions and the company's safety.
- Repeat, reinforce, remind. Training on security should not be a one-time event. It should be a series of regular sessions (for example, quarterly or annual). Vigilance fades without reinforcement.
- Democratize responsibility. Frame data protection as a collective mission, a shared duty, and then you will succeed.
Pillar 5: Secure Disposal & Redaction
Data has a lifespan. Ignoring its final stage - secure disposal - is like carefully locking a document in a vault and then throwing the key out of the window.
What to do:
- Destroy paper with purpose. Don't just toss documents in the recycling. Cross-cut and shred them. Make destruction bins as common as trash cans in areas handling sensitive paperwork.
- Delete data for good. Dragging a file to your computer's trash bin does not erase it. It just hides it. Use digital "shredding" software that overwrites the information, making it truly unrecoverable.
- Master the art of redaction. If the document that you are about to share includes employee confidential information that must not be seen, redact this information. For physical copies, you can use a black marker, for electronic documents - specialized AI-powered redaction tools.
Proactive Measures and Incident Response
Threats constantly evolve. Despite your best efforts, incidents will happen. A robust data protection strategy can minimize these incidents and suggest an action plan in case of a breach.
First, regularly audit your controls. A rule that goes unenforced quickly becomes a rule that doesn't matter. Consistency in accountability is what separates a policy document from an operational reality.
Second, create a breach response plan. It is not a matter of if the breach will happen; it is a matter of when. A breach response plan is a clear set of actionable steps that will make employees act in the right moment instead of panicking.
Your plan must cover how to contain the damage, assess the impact, fulfill legal notification duties, and, crucially, patch the vulnerability. When every second counts, this plan is your compass.
Conclusion
Protecting confidential employee information is a continuous commitment. It requires implementing comprehensive security measures for all sensitive information, including that beyond the usual personal identifiable data, and creating a robust breach response plan. Doing it, you’re not just checking a compliance box - you’re creating a safer, more secure workplace for everyone.
